Securing Your Outlook Calendar: Innovative, Outstanding, and Superior Privacy Strategies
Related Articles: Securing Your Outlook Calendar: Innovative, Outstanding, and Superior Privacy Strategies
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Securing Your Outlook Calendar: Innovative, Outstanding, and Superior Privacy Strategies. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Securing Your Outlook Calendar: Innovative, Outstanding, and Superior Privacy Strategies
Your Outlook calendar is more than just a scheduling tool; it’s a repository of your personal and professional life. Appointments, deadlines, travel plans – all sensitive information that needs robust protection. While Outlook offers some built-in privacy features, achieving truly outstanding and superior calendar privacy requires a multi-layered approach. This article explores innovative strategies beyond the basics, empowering you to control who sees what and when, ensuring your schedule remains confidential and under your complete command.
I. Beyond the Basics: Mastering Outlook’s Built-in Privacy Settings
Before diving into advanced techniques, let’s master Outlook’s inherent privacy controls:
-
Calendar Permissions: This is the cornerstone of calendar privacy. Instead of allowing everyone to see everything, meticulously manage permissions for each calendar you own. For personal calendars, consider these options:
- Free/Busy Only: This reveals only your availability (busy, free, tentative), hiding specific appointment details. Ideal for colleagues who need to schedule meetings without knowing the specifics of your commitments.
- Limited Details: Allows others to see the subject of your appointments, but not the details. A good balance between sharing availability and maintaining confidentiality.
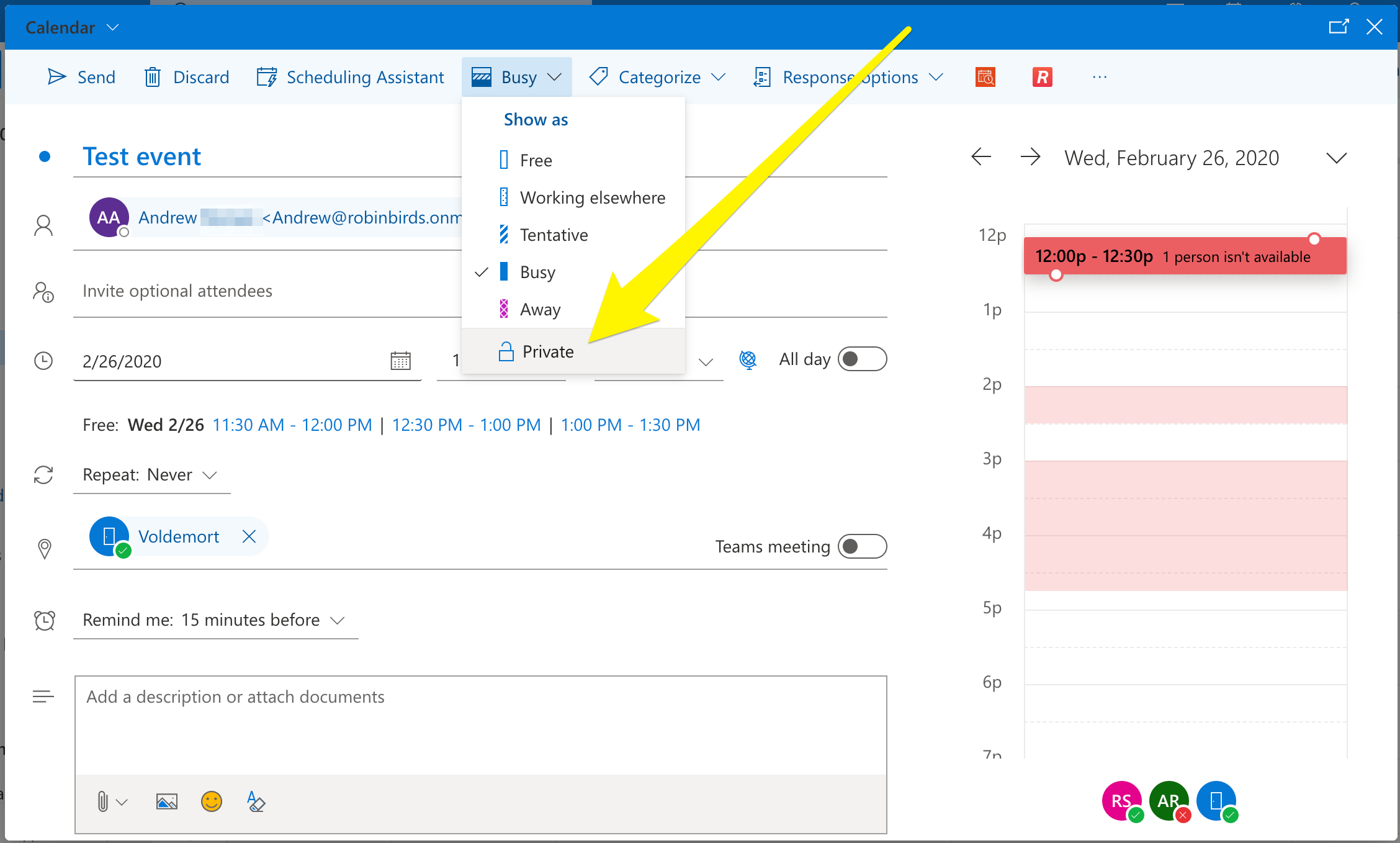
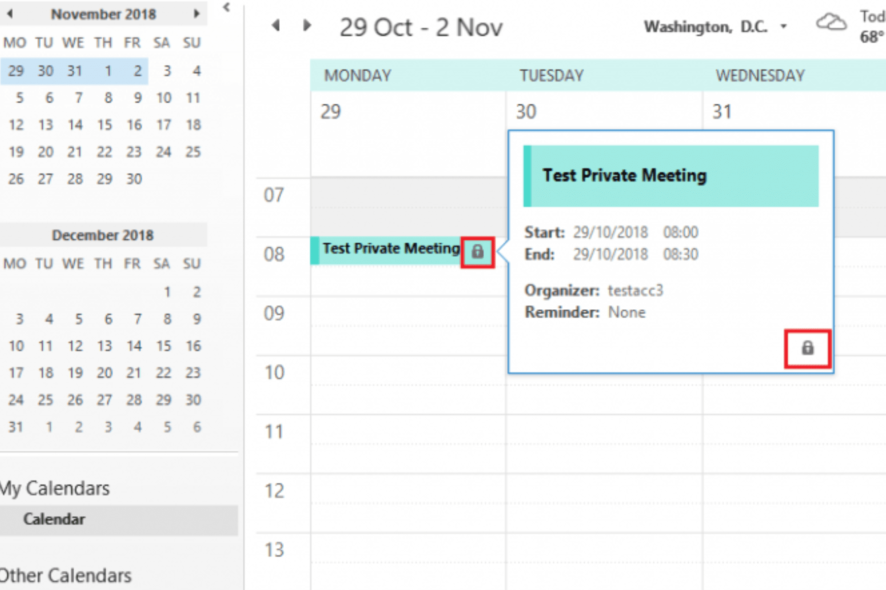
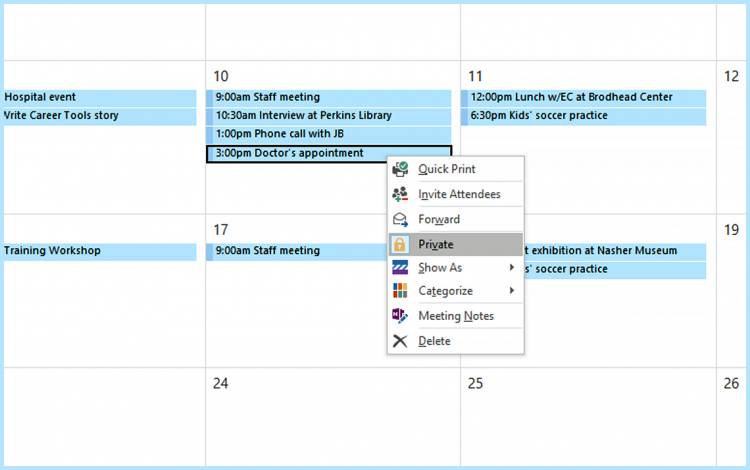
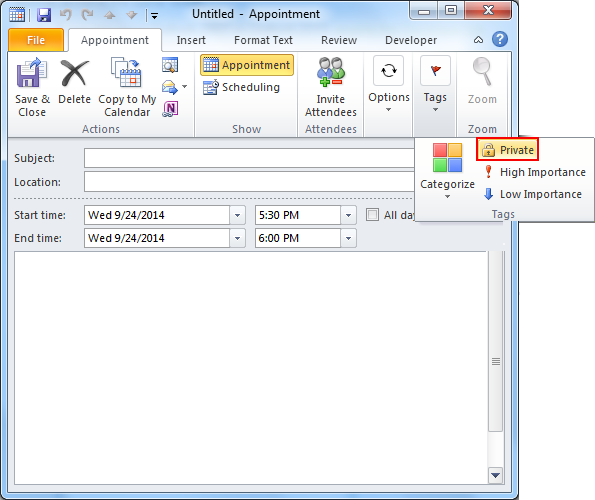
- No Access: The ultimate privacy setting, restricting access entirely. Use this for highly sensitive appointments or personal calendars you wish to keep completely private.
-
Delegates: If you grant delegate access to manage your calendar, carefully choose who receives these permissions. Clearly define their scope – can they create, edit, or delete appointments? Regularly review delegate access to ensure it aligns with your evolving needs.
-
Sharing Settings: Be mindful of how you share your calendar. Avoid sharing with large distribution lists unless absolutely necessary. Instead, share individually with specific individuals or groups. Consider using "anonymous" sharing for public events if appropriate.
-
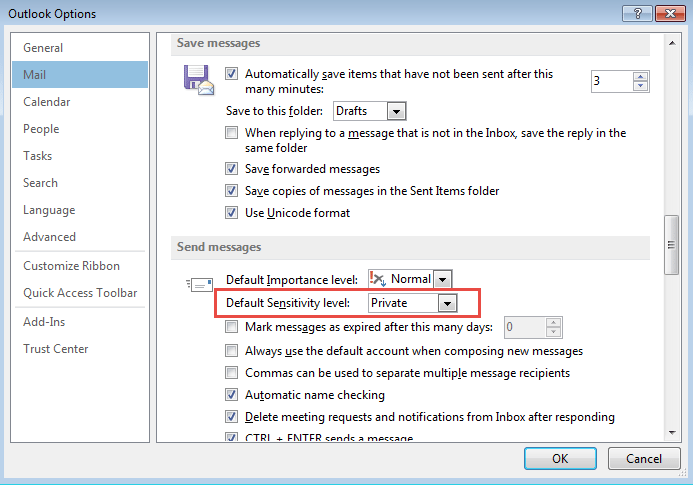
Password Protection (for PST files): If you store your calendar data in a Personal Storage Table (.pst) file, enable a strong password to protect it. This adds an extra layer of security if your computer is compromised.
II. Innovative Strategies for Enhanced Privacy
The built-in features are a starting point; true superior privacy necessitates innovative strategies:
-
Multiple Calendars: Divide your calendar into separate entities based on privacy levels. Create one for work, one for personal appointments, and perhaps another for highly sensitive information like medical appointments or financial meetings. This allows granular control over who accesses each aspect of your life.
-
Categorization and Color-Coding: Use categories and color-coding to visually separate sensitive appointments from public ones. This helps you quickly identify appointments that require extra caution when sharing your calendar.
-
Calendar Overlays: If you need to share a calendar with limited details, create an overlay calendar. This allows you to populate a public calendar with only the information you want to share, while keeping the complete details on a private calendar.
-
Regular Auditing: Periodically review your calendar permissions and sharing settings. Remove access for individuals who no longer require it or whose access is no longer relevant. This proactive approach prevents unintentional exposure of sensitive information.
III. Leveraging External Tools and Techniques
Going beyond Outlook’s built-in features unlocks further innovative privacy enhancements:
-
Two-Factor Authentication (2FA): Enable 2FA for your Microsoft account. This adds an extra layer of security, making it significantly harder for unauthorized individuals to access your calendar even if they obtain your password.
-
Strong Passwords and Password Managers: Use strong, unique passwords for your Microsoft account and any other accounts connected to your calendar. A password manager can help you generate and securely store these complex passwords.
-
Regular Software Updates: Keep your Outlook software and operating system updated. These updates often include security patches that address vulnerabilities that could be exploited to access your calendar.
-
Antivirus and Anti-malware Software: Install and maintain robust antivirus and anti-malware software on your devices. This protects against malicious software that could attempt to steal your calendar data or monitor your activity.
-
VPN Usage: Consider using a Virtual Private Network (VPN) when accessing your calendar from public Wi-Fi networks. A VPN encrypts your internet traffic, making it more difficult for others to intercept your data.
-
Encrypted Email: If you need to share sensitive appointment information via email, use end-to-end encrypted email services like ProtonMail or Tutanota. This ensures that only the sender and recipient can read the email’s content.
IV. Outstanding Practices for Superior Calendar Privacy
To achieve truly superior calendar privacy, adopt these outstanding practices:
-
Principle of Least Privilege: Grant only the minimum necessary access to your calendar. Avoid granting broad access unless absolutely essential.
-
Regular Backups: Regularly back up your Outlook data, including your calendar. This protects against data loss due to hardware failure, software corruption, or accidental deletion. Consider using cloud-based backup services for added security.
-
Device Security: Secure your devices with strong passwords or biometric authentication. This prevents unauthorized access to your calendar if your device is lost or stolen.
-
Awareness of Phishing Attacks: Be vigilant against phishing emails and other social engineering attacks that attempt to trick you into revealing your login credentials.
-
Privacy Policy Review: Review Microsoft’s privacy policy to understand how your data is collected, used, and protected.
V. Conclusion: Taking Control of Your Digital Life
Your Outlook calendar is a valuable asset containing sensitive information. Achieving truly outstanding and superior privacy requires a proactive and multi-layered approach. By combining Outlook’s built-in features with innovative strategies and external tools, you can significantly enhance your calendar’s security and maintain control over your digital life. Remember, proactive security measures are far more effective than reactive damage control. Regularly review and update your privacy settings to ensure your calendar remains a secure and private space for your scheduling needs. Prioritizing calendar privacy is not just about protecting your time; it’s about protecting your personal and professional well-being.
.jpg)
.jpg)
Closure
Thus, we hope this article has provided valuable insights into Securing Your Outlook Calendar: Innovative, Outstanding, and Superior Privacy Strategies. We appreciate your attention to our article. See you in our next article!